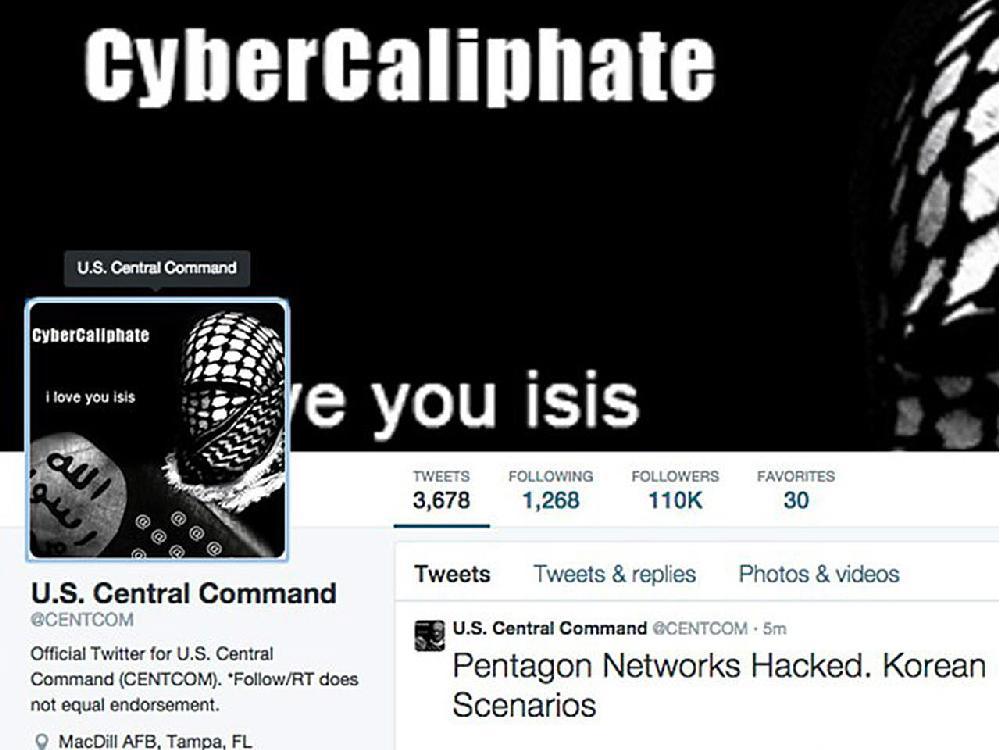
What does the hack of social media accounts for the U.S. military’s central command – by people claiming to be working with Islamic State (ISIL) militants – mean to Canadian governments and politicians? Here’s what you need to know.
1. A hacked Twitter account isn’t necessarily a threat to national security.
Merely breaking into a Twitter account doesn’t give hackers access to state secrets, because the service isn’t directly connected to internal government systems. But such hacks are embarrassing to the target organization, and damage reputations, while they also embolden malicious attackers, according to experts.
False tweets that go out on official accounts can have wide-ranging effects. For instance, in April 2013, the Associated Press news service had its Twitter account hacked, and a false tweet proclaimed: “Breaking: Two Explosions in the White House and Barack Obama is injured.” That message sent the Dow Jones Industrial average plummeting before the Associated Press announced the hack, and had its account suspended.
In November, the Canadian government launched a “digital diplomacy” initiative that focuses on diplomats using social media to engage people. Foreign Affairs Minister John Baird has been pushing Twitter diplomacy for almost a year. But these sorts of accounts could be targets for hackers wanting to embarrass the government.
2. But how a social media account is hacked could be a problem.
One of the most popular ways to hack a social media account is to go after users through emails that look safe, but have malicious software hidden inside. These “phishing” emails are difficult to defend against, and have become more complex. Once a target takes the bait, a hacker can gain access to a private network and sensitive information.
In Monday’s attack, the hackers did something public; that alerts security officials who can then track down the source of the breach, which is better than a hacker quietly moving around a system for days, weeks or months, says Mark Nunnikhoven, vice-president cloud and emerging technologies from security the firm Trend Micro.
3. Social media accounts don’t receive high security attention.
The federal government oversees 162 social media accounts, according to a government website, including 88 Twitter accounts, 28 YouTube channels and 36 Facebook pages. (That doesn’t include the accounts of MPs and senators.) Departments usually see these accounts as marketing and communications tools. Multiple people within a department may have to access accounts on a regular basis, leading to less complicated — and less secure — passwords.
“Organizations tend to think of their public relations sides as not being mission-critical,” says David Skillicorn, a computer security expert from Queen’s University.
“People don’t take their passwords seriously enough. It never surprises me that the password is 12345.”
4. There are things government can do.
The government doesn’t control the computer network running those social media services, meaning “they’re restricted by what Twitter or YouTube is able to do,” says Nunnikhoven. “You can’t add additional (layers of) encryption because it’s not your system.”
But departments can practise proper password hygiene, he says: Make passwords more complex; don’t use the same password for multiple accounts; and control who has access to the password itself. They should also limit the number of services linked with a Twitter, YouTube or Facebook account, Nunnikhoven says, just in case one of those services gets hacked, giving malicious actors a way into a Twitter account.
5. But we don’t know what the government actually IS doing.
No one from Treasury Board responded to questions about what, if any, measures the federal government is taking to prevent itself from being the subject of a hack similar to the one that hit U.S. Central Command on Monday.
http://ottawacitizen.com/news/politics/five-things-what-the-hack-of-the-u-s-militarys-twitter-account-means