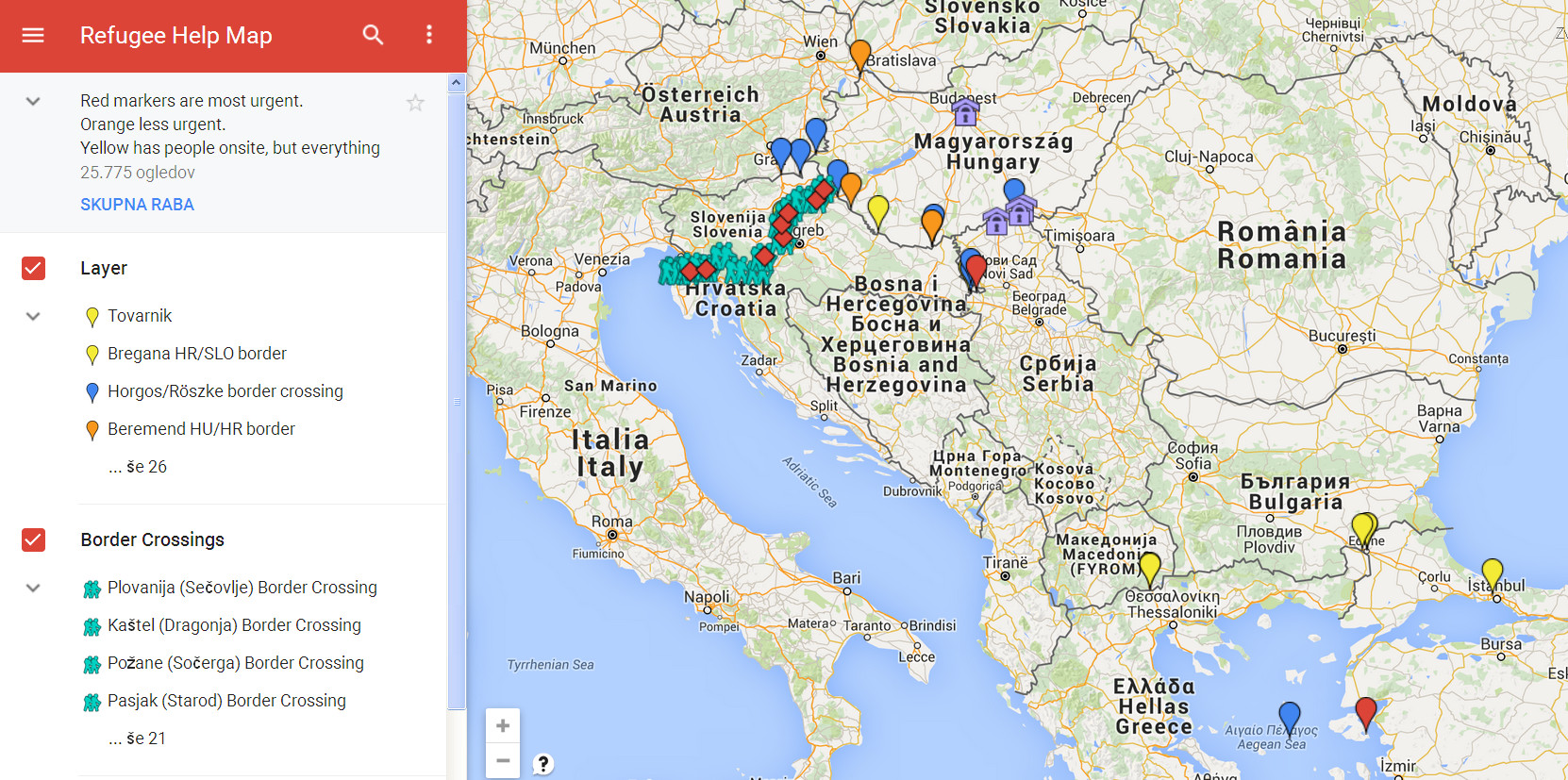
In the 2000s, “public diplomacy” became a central part of the function of diplomacy. As a result of the communications and transportation revolutions, diplomats, national leaders, and more can now be seen and heard by more people in more places than at any previous time in history. Skillful public diplomacy can influence public opinion beyond one’s own country to support policies and positions, and can influence foreign peoples to have a favorable view of one’s country. Conversely, blundering public diplomacy can undermine even well-conceived policies and positions, and can project an extremely negative image of a country.
Public diplomacy is important at other levels as well. Diplomats often seek and accept speaking engagements and media interviews, and work with other outlets in which they can obtain the opportunity to influence others to view their country and its policies favorably. At times, such public diplomacy may be considered by host countries as meddling in their internal affairs. At other times, such it may be virtually identical to a diplomat’s representation function. However, recently a new type of diplomacy, more malign, came into being.
On January 7, 2010, Google announced that it had been victim of a major hacker attack that began in mid-2009 and continued through December 2009. The attack, known as “Operation Aurora” and described by the largest search engine in the world as “sophisticated” and “high-level,” was aimed at more than 30 other organizations, including Adobe Systems, Rackspace, Yahoo, Symantec, Juniper Networks, Morgan Stanley, Northrop Grumman, and Dow Chemical.
In 2011, Google also said that the hackers, who were based in China’s Jinan province, had compromised personal email accounts of hundreds of top U.S. officials, military personnel, and journalists. Nobody has yet produced conclusive proof that such attacks were state-sponsored, but Google’s Press Office stressed that the primary goal of the hackers was to penetrate Google’s computers and access the Gmail accounts of Chinese human rights activists. Google also said that, apparently, the attack failed, as users’ data was not compromised.
More specifically, it appeared that the cyberattack was also conducted by advanced persistent threats carried out by the Elderwood Group—an organization based in Beijing, China, with ties to China’s Politburo, at least according to a U.S. State Department cables that WikiLeaks released in November 2010. Security experts have linked the attacks to servers at a university used by the Chinese military. Also, according to many computer specialists, the December 2009 attack, in terms of the style and instruments used, was very similar to the one perpetrated in July of the same year. The difference was that the second cyberattack targeted specific individuals. These attacks took advantage of some of the Google software’s vulnerabilities, which were still “unknown.”
Within hours of Google’s acknowledgment of the Aurora attacks, the U.S. State Department issued a statement asking the Chinese government for an explanation. Official Chinese media responded stating that the incident is part of a U.S. government conspiracy. For its part, Google decided to pull out of China and defied Chinese censorship regulations. It also moved further Chinese operations to Hong Kong, as it would have otherwise remained a constant target for Chinese cyberattacks.
These incidents led to diplomatic confrontations and raised profound questions about the future of online freedom and cybersecurity. Google, through former U.S Secretary of State Hilary Clinton, requested an official explanation from the Chinese government.
In a speech on Internet freedom, delivered on January 21, 2010 at the Newseum in Washington, DC and coming on the heels of the cyberattack, Clinton stressed the importance of freedom of information. In her own words, “as in the dictatorships of the past, governments are targeting independent thinkers who use these [internet, social networks] tools… As I speak to you today, government censors somewhere are working furiously to erase my words from the records of history. But history itself has already condemned these tactics.” Clinton’s remarks made it clear to online operators that the U.S. Government stands prepared to support them when they are willing to challenge the censorial policies of repressive foreign regimes.
China was cited numerous times in Clinton’s speech, especially with regards to its government’s policy on information. She concluded by saying that “historically, asymmetrical access is one of the leading causes of interstate conflict” and that “both the American people and nations that censor the internet should understand that our government is committed to helping promote internet freedom.”
Cyber security also dominated the first summit between Chinese President Xi Jinping and U.S. President Obama in June 7-8, 2013, Palm Springs, California. Obama confronted the Chinese president on the cyberattacks carried out from within Chinese borders throughout 2012 against nearly 40 Pentagon weapons programs. The Washington Post reported in May 2013 that compromised programs included missile defense systems, aircraft, and ships. Although the extent of official Chinese involvement cannot be clearly determined, U.S. officials have called upon the Chinese leadership to take a more active role in countering violations of cyberspace.
If the use of new technologies by governments is nothing new, especially in matters of espionage and control of public opinion, the scars wrought by the hacker attack can be considered the starting point of a new type of diplomacy—Cyber Diplomacy. Such technologies will continue to impact the geopolitical balance of power.
One novelty in terms of the Google and Pentagon weapons programs attacks is the high level of sophistication of these cyberattacks, which affected global leading companies in computer and information industries as well as the private lives of many powerful individuals around the world. Another feature is the immediate reaction coming from those placed in high level positions in the U.S. government, including the direct intervention of the Secretary of State. In her speech, she officially sanctioned the birth of Cyber Diplomacy, and highlighted computer security and freedom of the web as now crucial diplomatic issues. The economic, financial, industrial, and military sectors’ development and prosperity are increasingly linked to the free flow of information. Moreover, electronic networks are now irreplaceable instruments for international politics.
In addition to the traditional contentious issues between the United States and China—freedom of information, human rights, commercial rivalries, and the most recent agreement between Washington and Taiwan for continued military procurements—the Google episode is the prelude to further diplomatic confrontations. It places the two superpowers increasingly on an antithetical plane, even after the thaw initiated in 2008 with the election of Barack Obama.
Richard Rousseau is Associate Professor and Chair of the Department of Humanities and Social Sciences at the American University of Ras Al Khaimah, United Arab Emirates. His research, teaching and consulting interests include Russian politics, Eurasian geopolitics, international political economy, and globalization. He lived Three years in Baku, Azerbaijan.
http://www.diplomaticourier.com/news/regions/brics/1808-china-the-internet-and-the-birth-of-cyber-diplomacy